7. Accessing storage clusters via iSCSI¶
Acronis Cyber Infrastructure allows you to export cluster disk space to external operating systems and third-party virtualization solutions, in the form of LUN block devices over iSCSI in a SAN-like manner.
In Acronis Cyber Infrastructure, you can create groups of redundant targets running on different storage nodes. To each target group you can attach multiple storage volumes with their own redundancy provided by the storage layer. These volumes are exported by targets as LUNs.
Each node in a target group can host a single target for that group if Ethernet is used, or one target per FC port if Fibre Channel is used. If one of the nodes in a target group fails along with its target(s), healthy targets from the same group continue to provide access to the LUNs previously serviced by the failed target(s).
You can create multiple target groups on same nodes. A volume, however, may only be attached to one target group at any moment in time.
The figure below shows a typical setup for exporting Acronis Cyber Infrastructure disk space via iSCSI.
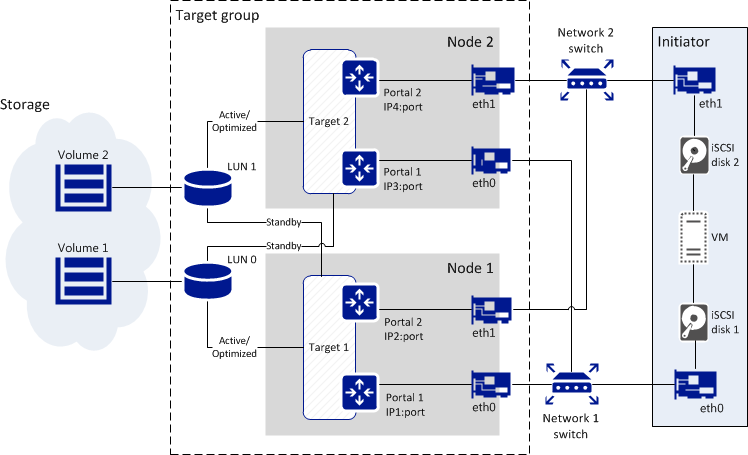
The figure shows two volumes located on redundant storage provided by Acronis Cyber Infrastructure. The volumes are attached as LUNs to a group of two targets running on Acronis Cyber Infrastructure nodes. Each target has two portals, one per network interface, with the iSCSI traffic type. This makes a total of four discoverable endpoints with different IP addresses. Each target provides access to all LUNs attached to the group.
Targets work in the ALUA mode, so one path to the volume is preferred and considered Active/Optimized while the other is Standby. The Active/Optimized path is normally chosen by the initiator (Explicit ALUA). If the initiator cannot do so (either does not support it or times out), the path is chosen by the storage itself (Implicit ALUA).
Network interfaces eth0 and eth1 on each node are connected to different switches for redundancy. The initiator, for example, VMware ESXi, is connected to both switches as well and provides volumes as iSCSI disks 1 and 2 to a VM via different network paths.
If the Active/Optimized path becomes unavailable for some reason (e.g., the node with the target or network switch fails), the Standby path through the other target will be used instead to connect to the volume. When the Active/Optimized path is restored, it will be used again.
In this chapter:¶
- 7.1. iSCSI workflow overview
- 7.2. Configuring CLI tool
- 7.3. Managing target groups
- 7.4. Managing iSCSI volumes
- 7.4.1. Creating iSCSI volumes
- 7.4.2. Listing and printing details of iSCSI volumes
- 7.4.3. Attaching iSCSI volumes to target groups
- 7.4.4. Setting the Active/Optimized path for iSCSI volumes
- 7.4.5. Viewing iSCSI volume ALUA information
- 7.4.6. Viewing and setting iSCSI volume parameters
- 7.4.7. Increasing iSCSI volume size
- 7.4.8. Setting iSCSI volume limits
- 7.4.9. Detaching iSCSI volumes from target groups
- 7.4.10. Deleting iSCSI volumes
- 7.5. Managing nodes in target groups
- 7.6. Managing targets and portals
- 7.7. Managing CHAP accounts
- 7.8. Managing LUN views
